Proxy Settings
The Proxy settings allow you to set parameters associated with the proxy service. These settings define:
- How clients will connect to the proxy on your network.
- How many system resources will be allocated to caching web content.
- Which content should bypass certain proxy features for compatibility etc.
ProTip: We strongly suggest reading the Concepts section in order to fully understand the options that are presented here.
General Settings
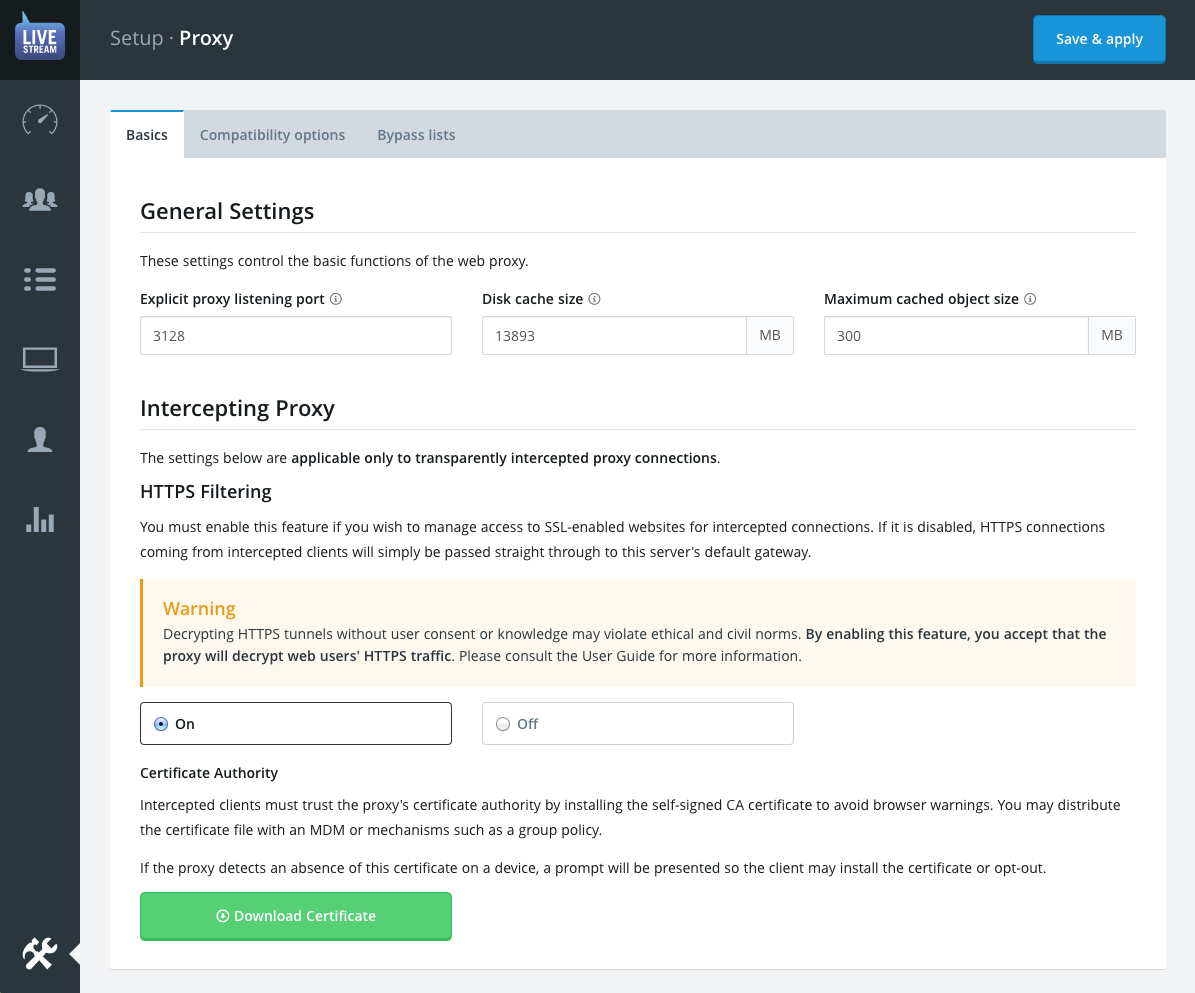
The explicit proxy listening port option allows you to customise which port will be open to receive explicit proxy connections. This is the port that will be specified in the proxy configuration(s) of client web browsers.
The standard proxy port is 3128, however many organisations prefer to use 8080.
Warning: Be careful not to use a port that's already reserved by another protocol.
Caching
As well as filtering content, LiveStream can also cache it. Whenever possible, it will cache (store) previously served web data so that subsequent requests for that data may be served from its cache rather than retrieving the request from the original source (the internet).
Caching can greatly improve browsing performance for end-users while reducing your organisation’s overall data usage with your ISP.
- The Disk cache size option allows you to set the amount of disk space the cache may use. The default setting for this field is 50% of the maximum (formatted) disk space, which is also the maximum amount the cache may use. This setting should only need to be changed in the event that disk space starts running low.
ProTip: Cache performance is tracked by the stats in Reports and on the Dashboard. Check out all the gigabytes you're saving!
- Maximum cached object size represents the largest any single cached file can be. If you want to include software updates and other large files set this to be over 1024 MB. If you would prefer to cache a wider range of smaller files, set this to be 64 MB or less.
Intercepting Proxy
Otherwise known as "transparent proxy" or "forced proxy"—an intercepting proxy behaves identically to an internet gateway, effectively performing NAT (Network Address Translation) but actually intercepts the web traffic for filtering and analysis.
LiveStream 5 operates as both an explicit proxy and an intercepting proxy, simultaneously.
- If a device's web traffic is routed through the LiveStream 5 proxy either by using it as their default gateway or by some kind of Layer 3 port redirection, then they will be using LiveStream 5's intercepting proxy mode.
- If the client has the proxy explicitly configured on their device either manually, via group policy or via an auto-configuration script (WPAD), then they will be using the explicit proxy mode.
As the system administrator, it's your responsibility to decide the manner in which the different types of devices on your network will connect to LiveStream 5. You can get in touch with Getbusi at any time for advice beyond what is presented here and in Deployment Options.
Warning: All non-web traffic will be ignored and passed-through by the NAT rules. Make sure that LiveStream 5's own gateway and logical network position does not allow clients to bypass their typical outbound connectivity restrictions.
HTTPS Filtering
As you have read previously in this guide, intercepting, decrypting and mimicking valid website certificates is a "necessary evil" when using an intercepting proxy.
When a client browser is explicitly using a proxy it will purposefully establish SSL connections in such a way that the proxy can maintain the client <---> website encryption tunnel. However, if the client browser's proxy is transparent it doesn't know that it should do this.
In order for an intercepting proxy to see any information about an HTTPS request (even the site hostname) it has to perform a man-in-the-middle violation. This would—ordinarily—trigger errors in the browser, suggesting to the user not to proceed.
Disclaimer: We realise this feature is ethically questionable, so it is disabled by default. It's left up to your organisation to determine the feasibility of the feature both technically and ethically.
Note that the only normally-encrypted information that LiveStream 5 will store is the full URLs of intercepted HTTPS requests. The contents of these pages is never stored or accessed by LiveStream.
Additionally, LiveStream will not mimic website certificates that are invalid. Actually invalid website certificate errors will be reproduced so that end users may still avoid potentially compromised web services.
When you enable HTTPS filtering in LiveStream, you are enacting a system called SSL Bump which handles every intercepted SSL connection accordingly:
- Detect that it's a SSL connection based on the port: 443
- Mimic the website's SSL certificate(s)
- Sign the "fake" website certificate(s) using your LiveStream proxy's self-signed certificate authority.
- Insert the "fake" certificates into the client's HTTPS response.
This process would obviously also cause browser warnings except if the client trusts the LiveStream proxy to sign all SSL certificates. To create this trust the client simply needs to install the CA certificate bundle (.cer) that LiveStream conveniently auto-generates when you enable the feature.
Once the cert bundle is downloaded from LiveStream 5 you may distribute it to devices via a domain group policy or MDM system.
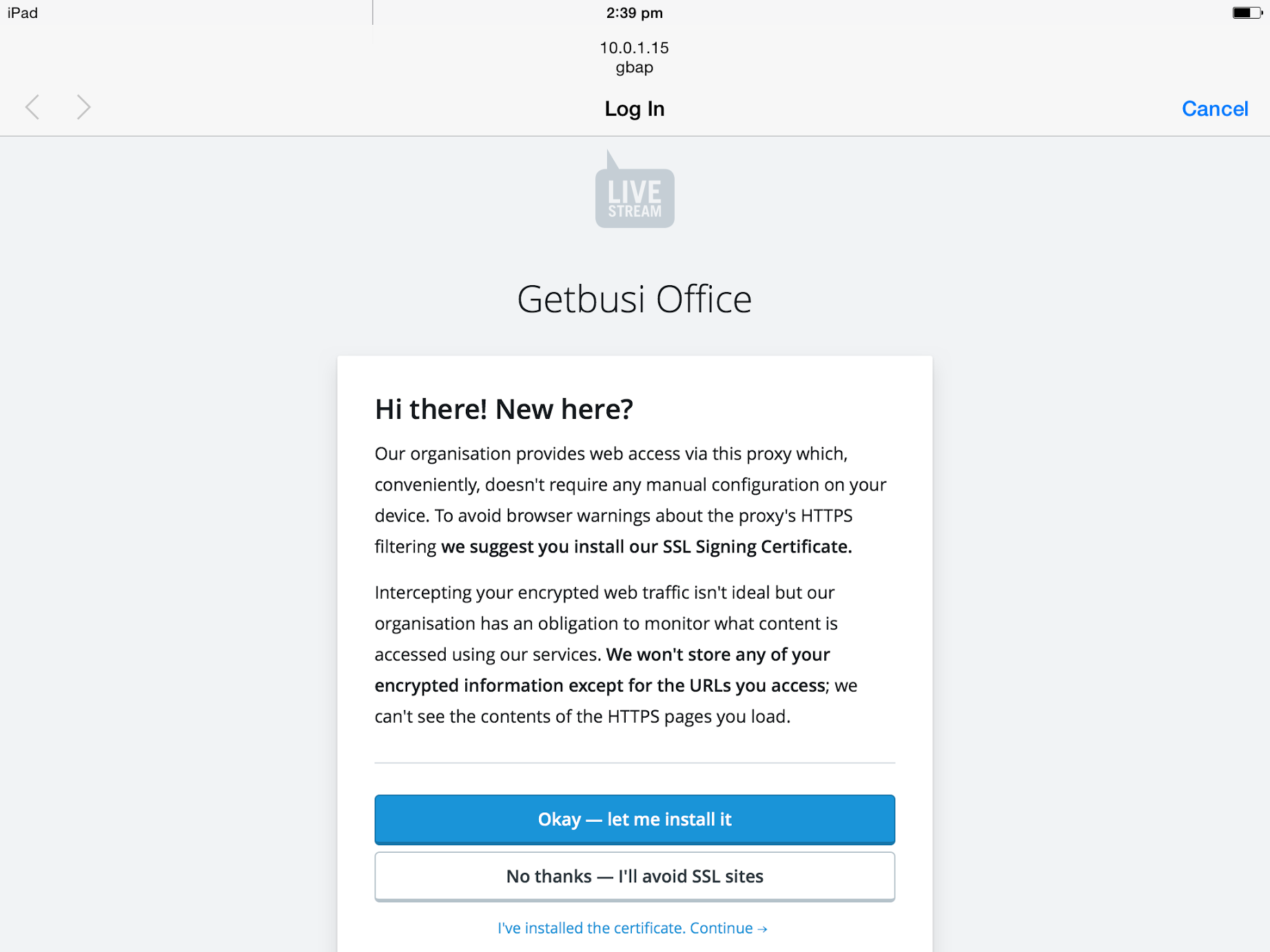
If you're dealing with BYOD, pre-distribution of the proxy certificate may not be practical. LiveStream has you covered by automatically probing intercepted clients for the presence of the certificate when they first access LiveStream. If they don't have it installed yet, they will be presented with a friendly splash page instructing them how to install or the certificate and why or, alternatively, opt-out and avoid HTTPS sites.
Compatibility options
Not all web-enabled applications were designed with web proxies and web filtering in mind. Chances are, if an application violates HTTP1.1 norms it may have trouble connecting via a proxy.
The compatibility options tab allows you to enable work-arounds for common applications and services that have known compatibility issues.
These definitions are maintained by Getbusi, based on testing, and are subject to sudden, unannounced changes by each vendor. If a compatibility option stops working for you, please contact support.
Compatibility definitions are currently maintained for:
- Certificate Revocation Lists
- Windows Update
- Apple iCloud and iTunes/App Stores
- Adobe updater
- Google Chrome updater
- Rover Browser for iOS
- Dragon Dictate for iOS
- Twitter App for iOS
ProTip: Getbusi would love to add more compatibility definitions. Drop us a line if you have an app or service you would like to suggest.
To enable a compatibility option, simply select the corresponding checkboxes and click save and apply.
Bypass lists
Bypass lists allows you to specify web resources which will not require certain proxy features in order to be accessed. This is an effective means to bypass compatibility issues with apps and services that don't have definitions maintained by Getbusi.
Bypass lists draw from the same List Groups as the rest of the system. Meaning you can bypass based on domain, IP, or subnet. List Groups are discussed later in the documentation.
ProTip: Determining what needs to be bypassed in order to get an application working is usually a matter of researching the app's proxy compatibility. Often, the vendor will provide instructions on how to configure the proxy to handle the app's connectivity quirks.
Authentication Bypass
The most common incompatibility is with web applications that do not support proxy authentication. This typically manifests itself with repeated prompts for authentication that cannot be avoided even by entering the valid credentials.
Cache Bypass
This can be used for highly dynamic web content which does not respond well to being cached. This will typically manifest itself with stale data being displayed.
Upstream Proxy Bypass
When an upstream proxy has been configured, requests to internet resources on the selected list will be made directly from LiveStream 5 to the website, bypassing the upstream proxy. This might be necessary for things such as internal websites that aren't accessible by the upstream proxy.
Creating a Bypass List
Under most circumstances you will want to create a specific list group for each type of Bypass.
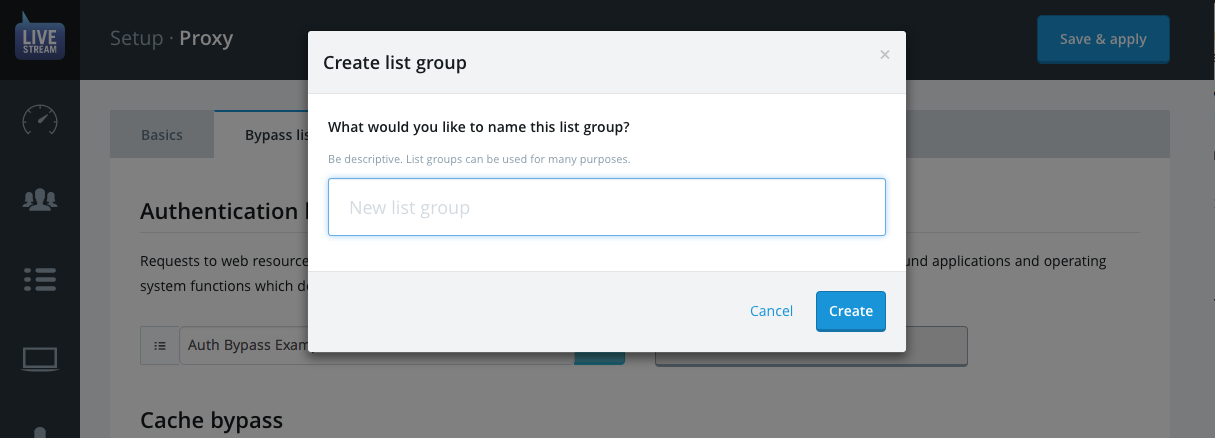
- Click the Create new filter list button.
- Enter a descriptive title for the list group in the dialogue form e.g. Authentication Bypass Content and click Create.
Editing a Bypass List
A Bypass List is just a list group like any other on the system, it is only a "bypass" list because you chose to apply it as such. You could also apply the same list to other rules, exceptions and bypasses.
You can edit a bypass list from the Proxy Settings or directly within the Lists section.
See the List Groups section for details on editing a list group.